There’s More Than Just Login Protection
Like to reset your password? Well, attackers try to do that, too. Therefore, online services should make sure that it’s really you who did that.
Risk-based authentication (RBA) checks during login whether a login attempt is a hacking attempt. Risk-based account recovery (RBAR) takes this idea further, and checks whether it is really you that tries to recover your account.
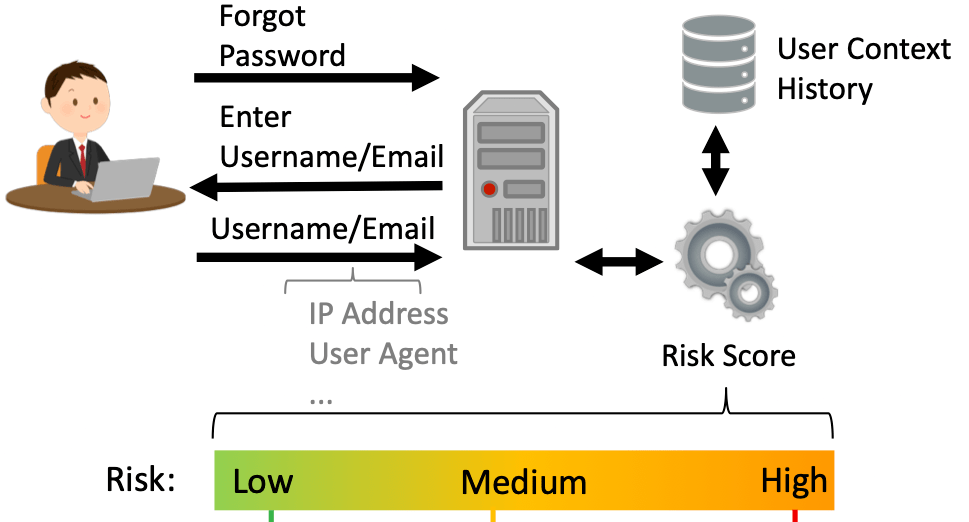
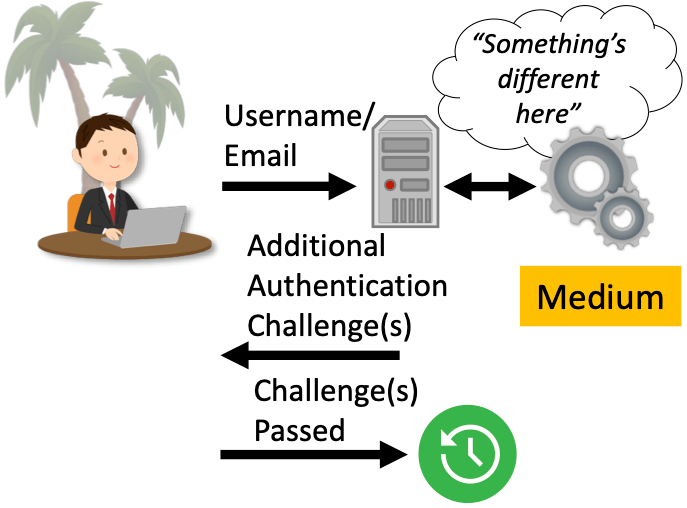
How It Works
After clicking the forgot password button, the user has to provide account details of the “lost” account. Then, RBAR will perform a risk analysis to estimate whether the request is an account takeover attempt.
When the risk is low, the account recovery process continues without further intervention.
When the risk is medium or higher, RBAR either requests an additional authentication challenge or blocks the recovery attempt. This allows RBAR to keep bad persons out while not bothering legitimate users.

Used By Popular Online Services
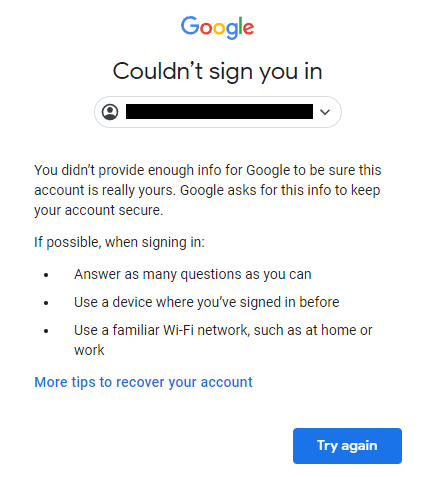
Studying popular websites, we found that Amazon, Google, and LinkedIn use RBAR in practice.
The implementations varied, from asking for an additional authentication factor, to answering background questions, to showing a CAPTCHA challenge.
Technical Paper
You can find more details in our publication below.
The paper is published at UbiSec ‘23.
Is It Really You Who Forgot the Password? When Account Recovery Meets Risk-Based Authentication
Andre Büttner, Andreas Thue Pedersen, Stephan Wiefling, Nils Gruschka, Luigi Lo Iacono
Read the paper AbstractAbstract
Risk-based authentication (RBA) is used in online services to protect user accounts from unauthorized takeover. RBA commonly uses contextual features that indicate a suspicious login attempt when the characteristic attributes of the login context deviate from known and thus expected values. Previous research on RBA and anomaly detection in authentication has mainly focused on the login process. However, recent attacks have revealed vulnerabilities in other parts of the authentication process, specifically in the account recovery function. Consequently, to ensure comprehensive authentication security, the use of anomaly detection in the context of account recovery must also be investigated.
This paper presents the first study to investigate risk-based account recovery (RBAR) in the wild. We analyzed the adoption of RBAR by five prominent online services (that are known to use RBA). Our findings confirm the use of RBAR at Google, LinkedIn, and Amazon. Furthermore, we provide insights into the different RBAR mechanisms of these services and explore the impact of multi-factor authentication on them. Based on our findings, we create a first maturity model for RBAR challenges. The goal of our work is to help developers, administrators, and policy-makers gain an initial understanding of RBAR and to encourage further research in this direction.
If you like to cite the paper, please use the following BibTeX entry:
@inproceedings{Buettner_Is_2024,
author = {Büttner, Andre and Pedersen, Andreas Thue and Wiefling, Stephan and Gruschka, Nils and {Lo Iacono}, Luigi},
title = {{Is It Really You Who Forgot the Password? When Account Recovery Meets Risk-Based Authentication}},
booktitle = {3rd {International} {Conference} on {Ubiquitous} {Security} 2023},
series = {{UbiSec} '23},
location = {Exeter, United Kingdom},
doi = {10.1007/978-981-97-1274-8_26},
publisher = {Springer},
month = mar,
year = {2024}
}