Improving Password Security
Using strong passwords doesn’t mean that your user account is safe. Large-scale password database leaks and intelligent password guessing attacks can still compromise your accounts.
Risk-Based Authentication (RBA) is an approach to improve account security on websites without forcing users to use Two-Factor Authentication (2FA).
How Does It Work?
During login, RBA estimates a risk score based on the login behavior.
- On a low risk (e.g. same device as always), access to the website is granted.
- On a medium risk (e.g. unknown device), the website asks for additional information to confirm the claimed identity (e.g. confirmation of email address).
- On a high risk, access is denied.
Who Uses RBA?
RBA is getting more and more important. We studied popular online services in 2018 and found evidence that Google, Facebook, LinkedIn, Amazon and GOG.com were the early adopters using it.
Want to know more about their state of practice?
Some online services even integrate mechanisms similar to RBA in their account recovery mechanisms, called risk-based account recovery (RBAR).
Want to find out more?
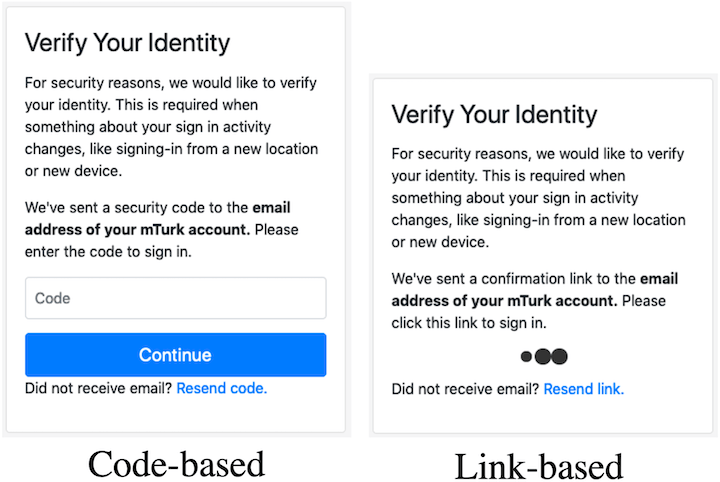
What’s the User Perception?
We studied this question with 65 users in our usability lab. The results show that
- Users mostly prefer RBA over 2FA.
- Users find RBA more secure than password-only authentication.
- RBA’s perceived security is comparable to 2FA.
However, these impressions strongly depend on the type of online service that deploys RBA. For more details:

How Does It Perform With Millions of Users?
We studied 3.3M users and 31.3M login attempts on a real-world online service to uncover the real world RBA behavior. The results indicate that:
RBA rarely asks legitimate users for re-authentication in practice, even when blocking targeted attackers.
For more results and the open data set with the login data:
Which Features Are Useful and What About Privacy?
Our observations of 780 users and ≈250 features over 1.8 years show that only few features are sensible for RBA. For the full analysis:
Users currently obtain RBA’s high security and usability benefits at the cost of disclosing potentially sensitive data.
However, it is possible to enhance privacy for RBA while maintaining security and usability properties:
HTTP client hints are a browser-based mechanism to increase privacy. Some RBA online services seem to use them as a feature in practice. Nevertheless, they might also be misused by third-party trackers.
Which Re-Authentication Method Should We Use?
On medium risk, users are asked for re-authentication.
But how long does this take and how do users feel about it? We tested three RBA re-authentication schemes with over 500 participants to find out more.
Want to know which scheme performs best?